The post AI Produces Data-driven OpenFOAM Speedup (HPC Wire) appeared first on Linux.com.
]]>The post AI Produces Data-driven OpenFOAM Speedup (HPC Wire) appeared first on Linux.com.
]]>The post Bridging Design and Runtime Gaps: AsyncAPI in Event-Driven Architecture appeared first on Linux.com.
]]>Various approaches exist for implementing asynchronous interactions and APIs, each tailored to specific use cases and requirements. Despite this diversity, these approaches fundamentally share a common baseline of key concepts. Whether it’s messaging queues, event-driven architectures, or other asynchronous paradigms, the overarching principles remain consistent.
Leveraging this shared foundation, AsyncAPI taps into a spectrum of techniques, providing developers with a unified understanding of essential concepts. This strategic approach not only fosters interoperability but also enhances flexibility across various asynchronous implementations, delivering significant benefits to developers.
From planning to execution: Design and runtime phases of EDA
The design time and runtime refer to distinct phases in the lifecycle of an event-driven system, each serving distinct purposes:
Design time: This phase occurs during the design and development of the event-driven system, where architects and developers plan and structure the system engaging in activities around:
- Designing event flows
- Schema definition
- Topic or channel design
- Error handling and retry policies
- Security considerations
- Versioning strategies
- Metadata management
- Testing and validation
- Documentation
- Collaboration and communication
- Performance considerations
- Monitoring and observability
The design phase yields assets, including a well-defined and configured messaging infrastructure. This encompasses components such as brokers, queues, topics/channels, schemas, and security settings, all tailored to meet specific requirements. The nature of these assets may vary based on the choice of the messaging system.
Runtime: This phase occurs when the system is in operation, actively processing events based on the design-time configurations and settings, responding to triggers in real time.
- Dynamic event routing
- Concurrency management
- Scalability adjustments
- Load balancing
- Distributed tracing
- Alerting and notification
- Adaptive scaling
- Monitoring and troubleshooting
- Integration with external systems
The output of this phase is the ongoing operation of the messaging platform, with messages being processed, routed, and delivered to subscribers based on the configured settings.
Role of AsyncAPI
AsyncAPI plays a pivotal role in the asynchronous API design and documentation. Its significance lies in standardization, providing a common and consistent framework for describing asynchronous APIs. AsyncAPI details crucial aspects such as message formats, channels, and protocols, enabling developers and stakeholders to understand and integrate with asynchronous systems effectively.
It should also be noted that the AsyncAPI specification serves as more than documentation; it becomes a communication contract, ensuring clarity and consistency in the exchange of messages between different components or services. Furthermore, AsyncAPI facilitates code generation, expediting the development process by offering a starting point for implementing components that adhere to the specified communication patterns.
In essence, AsyncAPI helps bridge the gap between design-time decisions and the practical implementation and operation of systems that rely on asynchronous communication.
Bridging the gap
Let’s explore a scenario involving the development and consumption of an asynchronous API, coupled with a set of essential requirements:
- Designing an asynchronous API in an event-driven architecture (EDA):
- Define the events, schema, and publish/subscribe permissions of an EDA service
- Expose the service as an asynchronous API
- Generating AsyncAPI specification:
- Use the AsyncAPI standard to generate a specification of the asynchronous API
- Utilizing GitHub for storage and version control:
- Check in the AsyncAPI specification into GitHub, leveraging it as both a storage system and a version control system
- Configuring GitHub workflow for document review:
- Set up a GitHub action designed to review pull requests (PRs) related to changes in the AsyncAPI document
- If changes are detected, initiate a validation process
- Upon a successful review and PR approval, proceed to merge the changes
- Synchronize the updated API design with the design time
- Set up a GitHub action designed to review pull requests (PRs) related to changes in the AsyncAPI document
This workflow ensures that design-time and runtime components remain in sync consistently. The feasibility of this process is grounded in the use of the AsyncAPI for the API documentation. Additionally, the AsyncAPI tooling ecosystem supports validation and code generation that makes it possible to keep the design time and runtime in sync.
Putting the scenario into action
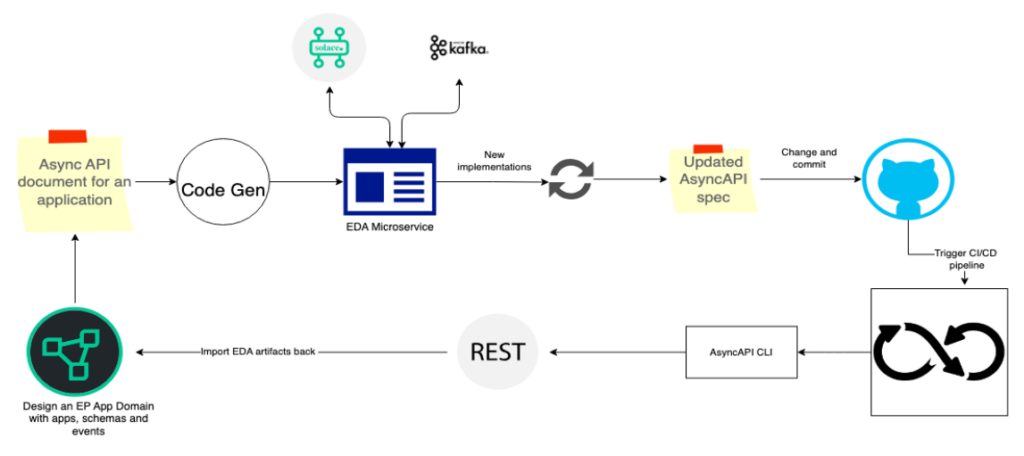
Let us consider Solace Event Portal as the tool for building an asynchronous API and Solace PubSub+ Broker as the messaging system.
An event portal is a cloud-based event management tool that helps in designing EDAs. In the design phase, the portal facilitates the creation and definition of messaging structures, channels, and event-driven contracts. Leveraging the capabilities of Solace Event Portal, we model the asynchronous API and share the crucial details, such as message formats, topics, and communication patterns, as an AsyncAPI document.
We can further enhance this process by providing REST APIs that allow for the dynamic updating of design-time assets, including events, schemas, and permissions. GitHub actions are employed to import AsyncAPI documents and trigger updates to the design-time assets.
The synchronization between design-time and runtime components is made possible by adopting AsyncAPI as the standard for documenting asynchronous APIs. The AsyncAPI tooling ecosystem, encompassing validation and code generation, plays a pivotal role in ensuring the seamless integration of changes. This workflow guarantees that any modifications to the AsyncAPI document efficiently translate into synchronized adjustments in both design-time and runtime aspects.
Conclusion
Keeping the design time and runtime in sync is essential for a seamless and effective development lifecycle. When the design specifications closely align with the implemented runtime components, it promotes consistency, reliability, and predictability in the functioning of the system.
The adoption of the AsyncAPI standard is instrumental in achieving a seamless integration between the design-time and runtime components of asynchronous APIs in EDAs. The use of AsyncAPI as the standard for documenting asynchronous APIs, along with its robust tooling ecosystem, ensures a cohesive development lifecycle.
The effectiveness of this approach extends beyond specific tools, offering a versatile and scalable solution for building and maintaining asynchronous APIs in diverse architectural environments.
Author
Post contributed by Giri Venkatesan, Solace
The post Bridging Design and Runtime Gaps: AsyncAPI in Event-Driven Architecture appeared first on Linux.com.
]]>The post Achieving Log Centralization and Analysis with Open Source SIEM and XDR: UTMStack appeared first on Linux.com.
]]>Technology and Architecture Overview
Deploying UTMStack for log centralization and analysis involves three main components: log collectors aka agents, a central server for log centralization, and correlation rules for detection and incident response.
Agents: These collect logs from systems and execute local and remote incident response commands. Agents can also function as proxies for collecting syslog and netflow logs from network devices.
Central Server: This server stores and correlates logs from various assets like other servers and firewalls to identify potential threats and orchestrates incident responses across the IT ecosystem.
Correlation rules and Incident Response: These detect possible threats to system security and availability by correlating logs from multiple systems with threat intelligence and predefined malicious sequences of behaviors and compromise indicators. Once a correlation rule evaluates a group of logs as potentially malicious, an alert triggers the incident response command.
Deploying the Open Source Security Stack
Log Centralization Server
The log centralization server can be deployed using an ISO image from the utmstack website for simplicity. For advanced installation options, please visit the official GitHub repository https://github.com/utmstack/UTMStack
Here are the instructions for installing without the ISO on Ubuntu Linux 22.04 LTS.
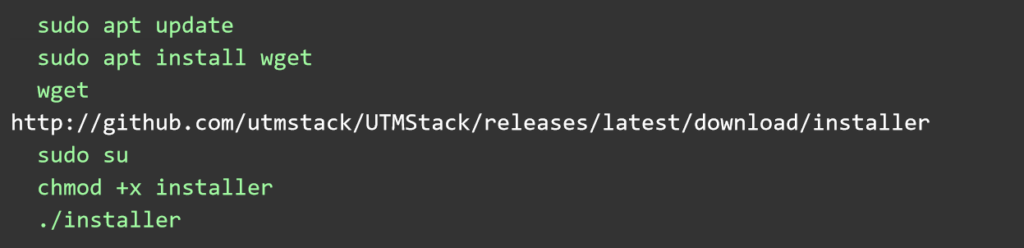
After installation, access the server via a browser using the server’s IP address or DNS name and the random secure password provided by the installer.
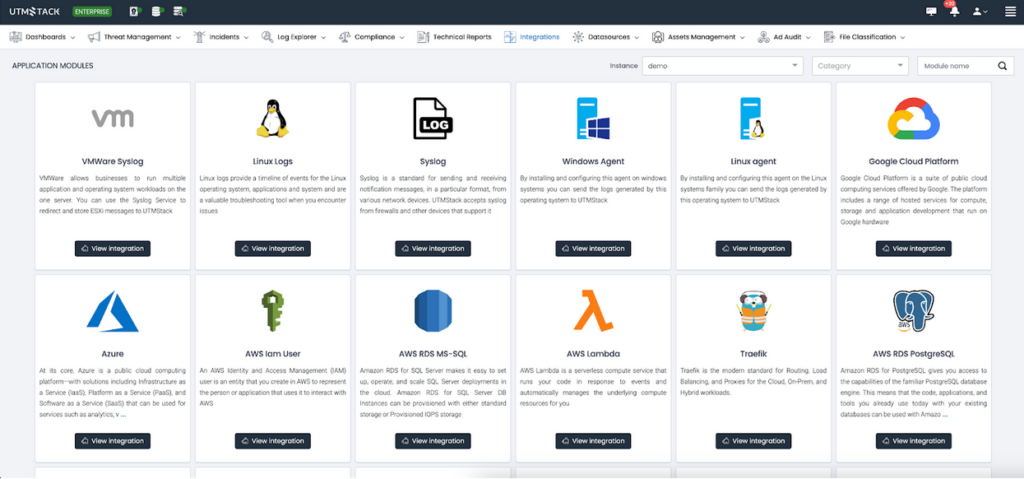
Deploying Log Collectors
Navigate to the “Integrations” section and select the appropriate agent for your operating system. Additional integrations can be configured as needed.
Defining Correlation Rules and Incident Response
Correlation rules form the core of a log management system, defining which logs or combinations thereof should trigger an alert or incident. UTMStack uses these rules as a basis for Incident Response playbooks.
Let’s take, for instance, a brute-force attack. This type of cybersecurity threat attempts to guess a user’s password by trying massive random combinations of characters until the correct sequence matches the user’s credentials. These types of attacks usually leave behind a trail of logs that indicate a user has failed to log into a system several times in a short period of time.
You can access the complete list of prebuilt correlation rules and the guide to creating new ones from the official UTMStack repository. For this guide, we’ll create a sample correlation rule to detect brute-force attacks.
UTMStack correlation rules are written in plain YAML and have three main components. Threat documentation that describes the rule, defines a tactic category of attack, severity and name of the rule. The second component is the logic and frequency block, where the rules for triggering this alert are defined. Finally, the alert information block, where the information is extracted from the logs and saved into the alert item.
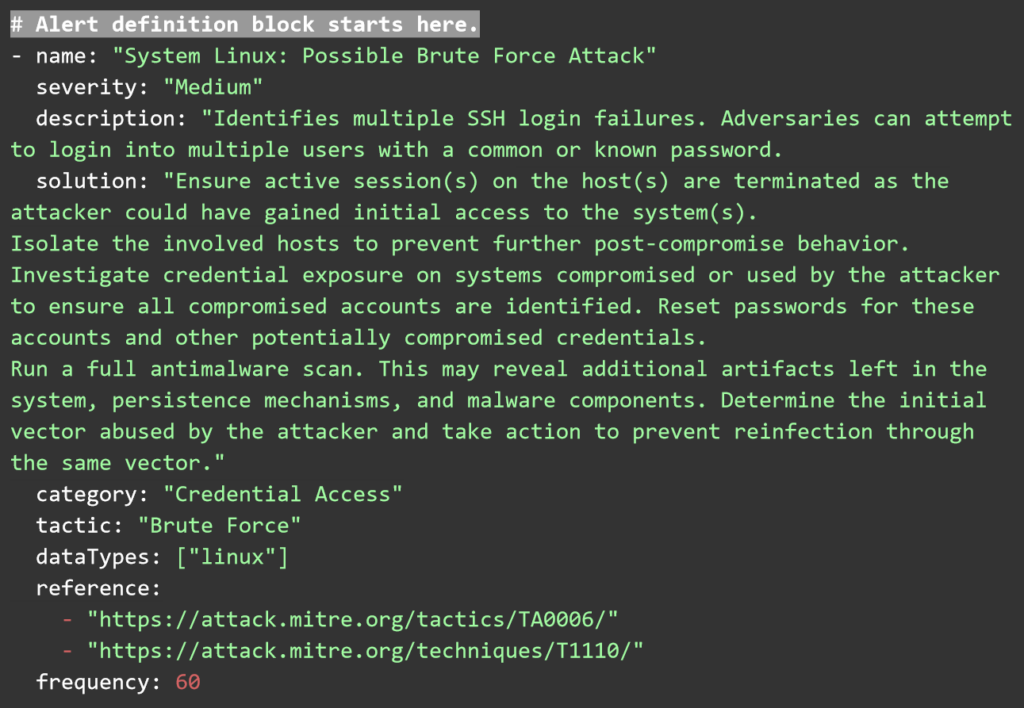
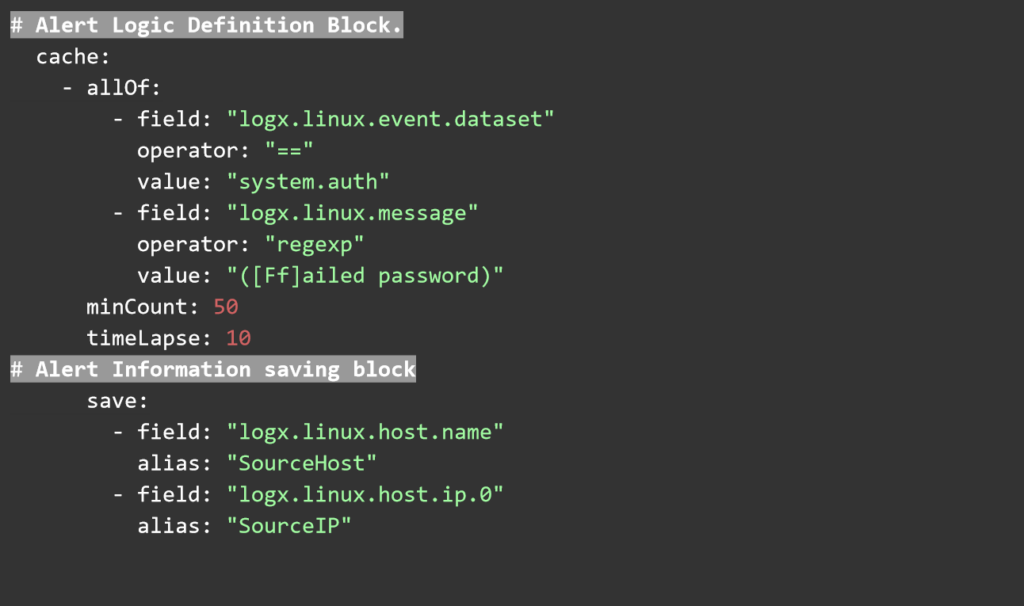
These YAML rules can be saved as text files and copied into the correlation rules folder via the Web User interface. Any rules uploaded there will be processed by the correlation engine automatically.
All logs the system receives are aggregated and correlated for indicators of compromise (IOCs) using several open threat intelligence feeds. This feature is enabled by default, and there is no need for custom correlation rules or configurations.
Finally, to deploy the incident response playbooks, navigate to the incident response automation section and drop a command to disable future login attempts from the offender host. This can be done by blocking its IP in the firewall or disabling the victim user until further investigation can be done.
UTMStack’s Incident response commands use dynamic variables to handle the execution of commands with different targets. Here are some examples.
Command to block a user:usermod -L ${source.user}
Command to block an IPiptables -A INPUT -s ${source.ip} -j DROP
Summary
Log centralization and analysis are essential for security, availability, and compliance. Open source tools can deliver advanced flexibility and rich feature sets to meet complex use cases and deliver an enterprise-ready experience. The UTMStack open source project is a powerful SIEM and XDR system that can deliver log management, threat detection and incident response by correlating and aggregating logs in real-time. Advanced features such as IOC detection, threat intelligence, and compliance are built-in features of the security stack.
Join Our Community and Contribute
We’re always looking for passionate individuals to contribute to our project. Whether you’re a developer, security expert, or just enthusiastic about cybersecurity, your input is valuable. Here’s how you can get involved:
GitHub Repository: Visit our GitHub repository to explore our code, submit issues, or contribute enhancements. Your code contributions can help us improve and expand UTMStack’s capabilities.
Discord Channel: Join our Discord community to discuss with fellow contributors, share ideas, and collaborate on projects. It’s a great place to learn from others and contribute your expertise.
Online Chat and Forums: For quick questions or discussions, use the online chat feature on our official website or the forums. It’s a direct line to our team and community for real-time interactions.
Your contributions, big or small, play a crucial part in the development and improvement of UTMStack. Together, we can build a stronger, more secure open-source SIEM & XDR solution. Join us today and help shape the future of cybersecurity!
Author

Rick Valdes
Founder, UTMStack
The post Achieving Log Centralization and Analysis with Open Source SIEM and XDR: UTMStack appeared first on Linux.com.
]]>The post Linux 6.8 Brings More Sound Hardware Support For Intel & AMD, Including The Steam Deck appeared first on Linux.com.
]]>Linux sound subsystem maintainer Takashi Iwai at SUSE describes the new sound hardware support for Linux 6.8 as:
“Support for more AMD and Intel systems, NXP i.MX8m MICFIL, Qualcomm SM8250, SM8550, SM8650 and X1E80100”
Read more at Phoronix
The post Linux 6.8 Brings More Sound Hardware Support For Intel & AMD, Including The Steam Deck appeared first on Linux.com.
]]>The post Linux 6.8 To Drop The SLAB Allocator, SLUB Optimizations Coming Too appeared first on Linux.com.
]]>Read more at phoronix
The post Linux 6.8 To Drop The SLAB Allocator, SLUB Optimizations Coming Too appeared first on Linux.com.
]]>The post Critical Bluetooth Flaw Exposes Android, Apple & Linux Devices to Takeover appeared first on Linux.com.
]]>Read more at darkreading.com
The post Critical Bluetooth Flaw Exposes Android, Apple & Linux Devices to Takeover appeared first on Linux.com.
]]>The post mkfs.ext4 – What it actually creates appeared first on Linux.com.
]]>Click to Read More at Oracle Linux Kernel Development
The post mkfs.ext4 – What it actually creates appeared first on Linux.com.
]]>The post Pipe and Splice appeared first on Linux.com.
]]>Click to Read More at Oracle Linux Kernel Development
The post Pipe and Splice appeared first on Linux.com.
]]>The post Syscall latency… and some uses of speculative execution appeared first on Linux.com.
]]>Click to Read More at Oracle Linux Kernel Development
The post Syscall latency… and some uses of speculative execution appeared first on Linux.com.
]]>The post sos report – The Swiss Army Knife of Diagnostic Tools appeared first on Linux.com.
]]>Click to Read More at Oracle Linux Kernel Development
The post sos report – The Swiss Army Knife of Diagnostic Tools appeared first on Linux.com.
]]>